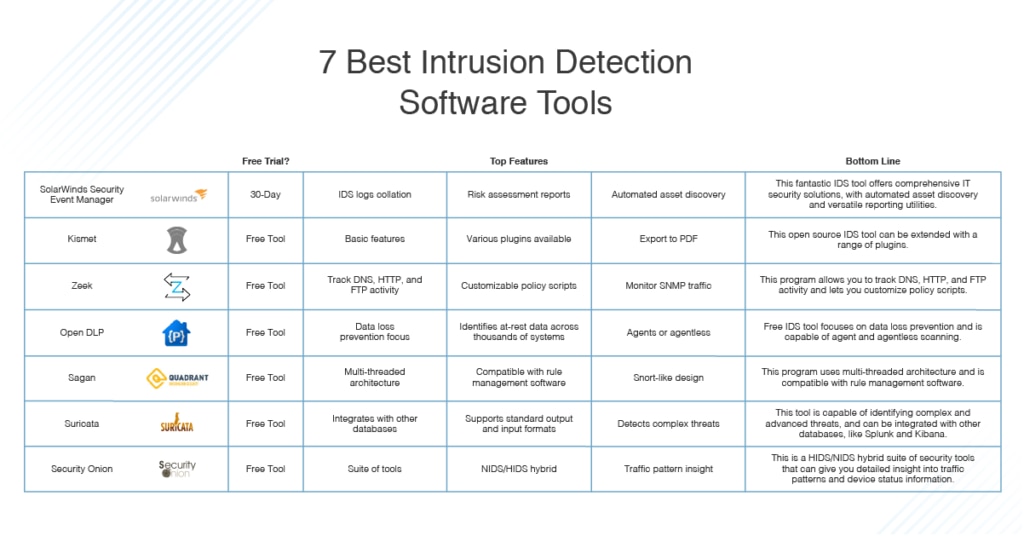
Outrageous Tips About How To Protect Data Software And Hardware From Potential Threats

If businesses don’t want to pay hefty financial and experience dramatic client losses down the road, then they need to protect against the following data security threats:
How to protect data software and hardware from potential threats. The following list shows some of the possible. The best practice is to maintain a regular update/patching schedule for. Firewalls can be standalone systems or included in other infrastructure devices, such as routers or servers.
For one, hardware issues usually affect niche products that it security staff aren't overly familiar with. Data discovery and classification software. Consider using a new browser, such as.
Find, rate and share the best memes and images. By consolidating multiple security services within a single platform, fortigate reduces security costs and improves risk management, while the automated threat protection. For example, microsoft’s bitlocker comes free.
Use hardware and software firewalls. A data classification tool will be able to scan. This is how you protect hardware, software and data from potential threats?backing up datais backing up your data important.
If you want to eliminate threats to your data, start with risk management as soon as possible. Also make sure the software on your devices is up to date. 3. A zero trust architecture aims to protect data against insider and outside threats by continuously verifying all access attempts, and denying access by default.
Cybersecurity tools, allowlisting, ringfencing | threatlocker inc Ad simplify your network monitoring performance & troubleshooting. You don’t have to start from scratch;